Part 2: How Do We Take Care of Our Students, Ourselves?
Ask What You Want; We Don’t Know Who You Are: Live Chat, Library Anxiety, and Privacy in an Academic Library
Bridgette Sanders; Jon B. Moore; and Kimberly Looby
Virtual reference services have evolved over the last 20+ years and are now a significant part of many libraries. According to the Reference and User Services Association (RUSA), “Virtual reference is a service initiated electronically for which patrons employ technology to communicate with public services staff without being physically present. Communication channels used frequently in virtual reference include chat, videoconferencing, Voice-over-IP, co-browsing, e-mail, instant messaging, and text” (RUSA, 2017). Chat has been an effective means of contact by patrons to their library for many years. It allows patrons to ask questions quickly and efficiently without calling or speaking with someone. This may reduce patron uneasiness and library anxiety, which is the “uncomfortable feeling or emotional disposition experienced in a library setting that has cognitive, affective, physiological, and behavioral ramifications” (Jiao & Onwuegbuzie, 1997, p. 372).
In the literature of library science, one recognizes the interplay between embarrassment and asking for help as a well-known feature of library anxiety. Librarians often consider live chat as one way of alleviating library anxiety because of its remote access and enhanced anonymity (Brown, 2011; Fagan & Desai, 2002; Gray, 2000).
Today’s students also witness and experience rampant privacy violations from online platforms. Contrary to claims that younger generations care less about privacy, evidence indicates that young people in the US as recent as millennials are as concerned about privacy as older generations (Hoofnagle et al., 2010). When asked, younger people who don’t use virtual reference services have listed privacy concerns as one reason (Connaway et al., 2011; Mawhinney, 2020). Their concerns may be well-founded; the anonymity afforded by online chat is not absolute.
When students come to a university, they are navigating new issues with privacy daily, which may increase their concern for privacy. Many students are making unfamiliar decisions about giving away their personal information, such as registering for services that may include loans, bills, medical care, and banking (Akhtar & Abbasi, 2019; Givens, 2015; Keizer, 2012). Students will also be greeted with scams such as phishing, social media scams, romance scams, and other attempts at stealing their information (Hanoch & Wood, 2021; Mustofa, 2020; Sorrell & Whitty, 2019; Sutton, 2022). Since libraries are part of the ecosystem of university life, libraries should take steps to ensure the privacy of their students.
Like other online information technologies, some chat platforms automatically gather data about users that they might not otherwise share. For instance, it is not uncommon for chat platforms to gather a user’s IP address, which can be connected to “geographic data elements such as city, state, zip code, and possibly even the name of a specific institution or Internet service provider through which the user is accessing the Internet” (Mon et al., 2009). Some libraries may design their chat system to proactively seek personally identifiable information as a pre-condition for beginning the reference transaction (Nolen et al., 2012).
There have also been many studies conducted to analyze chat transcriptions for various purposes. Recent articles used chat transcripts and statistics to determine satisfaction or dissatisfaction with chat services. Logan et al. (2019) conducted a study to identify behaviors that contribute to user dissatisfaction and recommend improvements. In Mavodza (2019), the patterns and types of questions being asked and the number of times they were asked were used to interpret chat transactions for staffing purposes and to “organize live chat guidelines in accordance with patron needs.” An earlier study examined face-saving communication (methods of reducing embarrassment or perceived loss of social standing) in chat transcripts by librarians and whether it lowered patron anxiety (Owens, 2013).
It is reasonable to ask whether these factors—which are also seen in other online information technologies familiar to students—are associated with privacy concerns that suppress a library-anxious student’s preference for remote help from chat.
Research Question and Objective
To investigate this problem, the authors sought to answer the question: What relationship exists between students’ library anxiety and privacy attitudes in the context of library live chat services? Because little previous research has explored this question, the authors approach the topic from several angles to establish a foundation for future research. This analysis includes:
- The authors’ experiences with chat as reference librarians
- An exploration of theoretical perspectives of library anxiety and privacy attitudes
- A discussion of an empirical investigation connecting theory to real-world data
The authors hope that this chapter can encourage future research into the topic of the privacy behaviors of student users of libraries by providing useful analytical tools.
Library Live Chat at UNC Charlotte
To give context to this study, it will be helpful to describe the university and library where this research took place. The University of North Carolina at Charlotte (UNC Charlotte) is the largest university in the Charlotte region and the third largest of 17 institutions in the UNC System. UNC Charlotte is a research-intensive institution with more than 30,000 undergraduate and graduate students and over 1,000 full- and part-time faculty. The J. Murrey Atkins Library at UNC Charlotte is one of the largest research libraries in North Carolina with a permanent staff of about 90. The Research and Instructional Services (RIS) unit consists of 15 full-time librarians. These librarians are responsible for liaison and collection development duties in addition to staffing the Information and Research Desk, where research services are provided. This desk is also staffed by Access Services employees who primarily check out materials and equipment. In design, Atkins Library follows a common reference model described in Gotschall et al. (2021), in which the front desk at the library entrance, in addition to being the primary point of contact for circulation, is also where users might ask reference questions or schedule meetings with reference librarians.
Atkins Library has been providing a virtual chat reference service since the early 2000s. Virtual reference services have primarily been the responsibility of the library’s research librarians, although Atkins Library has used several different staffing models over the years. Atkins Library has also used various chat systems including QuestionPoint, Libraryh3lp, and currently the Springshare platform LibChat.
When beginning a chat in LibChat, users are given the option to include their name or to leave the name field blank to remain more anonymous to the library employee. The employee they are chatting with may or may not be anonymous to the user depending on whether the employee is signed in with their individual account or under a shared department account.
There have been internal conversations about whether displaying librarians’ names makes the chat service more personal for the user and whether being more personal is desirable. Chat can give a level of anonymity on both ends that cannot be guaranteed in face-to-face interactions. It is an impersonal space that anonymizes people who may often know each other. If anonymity is the goal, personal connection could be counterproductive. For example, many faculty ask questions directly to their subject librarians, but in the authors’ experience, some are hesitant to ask questions because they may feel embarrassed for not knowing information they feel they should know. These faculty have implied that they use chat to ask such questions anonymously. Sometimes, library employees may recognize faculty members on chat either by their question or by their name, if shared. In trying to be friendlier and more personal, should the library employee reveal to these faculty seeking anonymity that they do, in fact, know who they are? Would they prefer to know that the person hearing their question is a friendly face, or would asking a potentially embarrassing question to someone you know feel even more embarrassing? This shows the intricacies of protecting patrons’ privacy and balancing the anonymity of library employee and patron interactions, especially for users who have anxiety about their questions.
Theoretical Foundations
In the earliest literature of library anxiety, library anxious students were observed to fear that asking questions of a librarian will reveal personal inadequacy or incompetence, and that this will result in negative judgement from the librarian (Bostick, 1992; Kuhlthau, 1988, 1991; Mellon, 1986). In this chapter, this phenomenon is labeled perceived interpersonal threat (PIT). This PIT, which is associated with feelings of shame (McAfee, 2018) and moderated by many situational and social factors (Jan et al., 2020; Jiao & Onwuegbuzie, 1997, 1998, 1999, 2002), inhibits the library anxious student’s willingness to seek interpersonal help.
The practical literature of reference librarianship includes strategies to reduce library anxiety by reducing the effect of the PIT by various means, (Carlile, 2007, p. 139; Mavodza, 2019; Onwuegbuzie et al., 2004 pp. 268–274) including live chat (Fagan & Desai, 2002; Gray, 2000). However, the effect that live chat services have on library anxiety is difficult to understand using Mellon’s (1986) original framework and to measure using the standard Library Anxiety Scale developed by Bostick (1992) because neither incorporate more modern-day computer technologies that allow for remote assistance (Anwar et al., 2004, p. 280; Jiao & Onwuegbuzie, 2004, p. 139; Katapol, 2012, p. 8; Kwon, 2008, p. 120; Van Kampen, 2004, p. 29). To correct for this, this study instead uses Erfanmanesh et al.’s (2012) Information Seeking Anxiety Scale (ISAS), which has been used in a number of studies (Aghaei et al., 2017; Erfanmanesh, 2016; Erfanmanesh et al., 2014; Khan et al., 2021; Naveed & Ameen, 2016a, 2016b, 2016c, 2017a, 2017b; Rahimi & Bayat, 2015). The ISAS is best understood as an instrument to measure the phenomenon of information seeking anxiety (ISA) specifically among students in the academic context where the library continues to play a role, but where information seeking may also happen outside the library building (Erfanmanesh, 2012, p. 22).
To understand the privacy component of this study, the authors use the specific lens of information privacy, as distinguished from physical or general privacy, because this framework is most relevant when discussing “access to individually identifiable personal information” (Smith et al., 2011, p. 990). Information privacy concern (IPC) is the primary construct through which an individual’s relationship to information privacy is measured (Malhotra et al., 2004; Smith et al., 1996). Like library anxiety, considerable evidence asserts that IPC is moderated by situational and social factors (Altman, 1977; Kayhan & Davis, 2016; Okazaki et al., 2012; Ozdemir, 2017; Petronio, 2002; Taylor & Altman, 1975; Waldo et al., 2010; Xu et al., 2011).
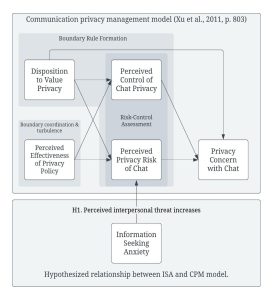
The measurement scales proposed by Xu et al. (2011) provide the most suitable instruments for measuring how social dynamics between individuals and institutions affect the individual’s IPC. These instruments build on Communication Privacy Management (CPM) theory, which holds that an individual negotiates their decision to reveal private information using, among other variables, their perception of how much risk is associated with potential privacy breaches and how much control they retain over future information sharing (Petronio, 2002). Potential interpersonal privacy risks may include threats of stigma, “the assumption that others might negatively evaluate behaviors or opinions of an individual,” or face, “situations where our disclosures cause us embarrassment, embarrass others in our group” (Petronio, 2002, p. 70), which overlap heavily with the feelings associated with library anxiety in students.
Hypotheses
If the predictions of communication privacy management theory, library anxiety theory, and information seeking anxiety theory are accurate, one should observe a particular effect occurring between information seeking anxiety and the perceived privacy risk of using live chat. One would expect to see that, like with general library anxiety, higher information seeking anxiety in a student creates a perception that library employees represent an interpersonal threat of embarrassment, judgment, or shame. This perceived interpersonal threat targets fears related to stigma risks and face risks as described by Petronio (2002). Because live chat involves interpersonal communication with a library employee, these risk perceptions would also carry over to the remote context of live chat. When the student judges the privacy safety of live chat by assessing its privacy risks vs. their privacy control, one would therefore expect them to perceive the use of live chat as being riskier. This hypothesis may be summarized as:
H1. Higher information seeking anxiety affects the students’ risk-control assessment regarding live chat privacy by increasing the perceived risk.
The null hypothesis of H1 may be stated as:
H10. Information seeking anxiety has no effect on the students’ risk-control assessment of privacy.
Combining this hypothesis with the full communication privacy management model discussed in Xu et al. (2011) results in the proposed model visualized in Figure 1.
Methods
To test H1 and future hypotheses related to the relationships between ISA, privacy attitudes, and library live chat, the authors constructed a dataset which uses the Information Seeking Anxiety Scale (ISAS) described in Erfanmanesh et al. (2012) and the privacy attitude measurements described in Xu et al. (2011). To build this dataset, the authors distributed an IRB-reviewed survey by email using Qualtrics.com to a stratified random sample of undergraduate and graduate students at or above the age of 18 at UNC Charlotte. Respondents were offered a chance to win one of six $15 gift cards via random drawing as an incentive to participate. Contact information for the random drawing was collected separately from the survey.
Respondents were asked to provide the demographic information of age range, racial and ethnic identity, gender identity, and year in school. They were asked to estimate their likelihood of using live chat with their university library and with other non-university services. They were asked to complete the ISAS instrument. Finally, they were asked to respond to instruments measuring privacy concerns with chat (hereafter: CONC), perceived privacy risks of chat (RISK), perceived privacy control over chat data (CTRL), perceived effectiveness of privacy policy (POLI), disposition to value privacy (VALU), awareness of privacy issues (AWAR), and previous privacy experience (PEXP). Because there is no comparable institutional self-regulation standard as described in Xu et al. (2011), that instrument was omitted.
Minor alterations were made to the language of the instruments from Xu et al. (2011) to specify live chat as the online service being analyzed and the university library as the relevant institution. The scale values were reduced from 7 to 5 to match the values used in ISAS. Minor alterations were made to the language of the ISAS to match vocabulary and phrasing to regional expectations.
The survey gathered 540 responses. Eight were identified as invalid and removed. Due to an error in the survey, too few usable responses were received to one item of the ISAS; responses to this question were removed. A subsequent analysis of the missing values determined that only 0.9% of respondents did not complete the survey in full, and only 0.3% of non-demographic values were missing. No pattern was discovered in these values. Missing demographic values were re-coded as “Prefer not to say.” Predictive mean matching with k=5 nearest neighbors was used to impute the other missing values in the final data. The final dataset includes 532 complete responses.
Table 1. Demographic Representation in Sample Compared to University PopulationTable note. Under Race and Ethnicity, AIAN abbreviates “American Indian or Alaska Native,” NHOPI abbreviates “Native Hawaiian or Other Pacific Islander,” and PNS abbreviates “Prefers not to say.” Data about university demographics at UNC Charlotte were gathered from the UNC Charlotte Institutional Research Analytics Fact Book at https://ir-analytics.charlotte.edu/fact-book.a Respondents provided more specific values for age range—25–34, 35–49, and 50+—but these values are presented together to facilitate a more direct comparison to university figures.
Table 1. Demographic Representation in Sample Compared to University Population
| Demographic Category | |||
| Age Range | Sample Frequency | Sample Percent | University Percent |
| 18–24 | 404 | 75.9% | 75.9% |
| 25+a | 128 | 24.1% | 23.2% |
| Prefer not to say | 1 | 0.2% | – |
| Race and Ethnicityb | |||
| AIAN | 10 | 1.9% | 0.2% |
| Asian | 116 | 21.8% | 8.3% |
| Black or African American | 60 | 11.3% | 16.2% |
| Hispanic or Latino | 60 | 11.3% | 11.3% |
| NHOPI | 2 | 0.4% | 0.1% |
| White | 339 | 63.7% | 51.3% |
| Unknown/PNS | 24 | 4.5% | 1.8% |
| Gender Identity | |||
| Woman/Female | 302 | 56.8% | 50.1% |
| Man/Male | 173 | 32.5% | 49.9% |
| Different Response | 16 | 3.0% | – |
| Prefer not to say | 41 | 7.7% | – |
| Class Status | |||
| Freshman | 60 | 11.3% | 11.7% |
| Sophomore | 92 | 17.3% | 16.8% |
| Junior | 115 | 21.6% | 22.3% |
| Senior | 127 | 23.9% | 25.8% |
| Graduate Student | 130 | 24.4% | 20.8% |
| Other | 5 | 0.9% | 2.2% |
| Prefer not to say | 3 | 0.6% | – |
a Respondents provided more specific values for age range—25–34, 35–49, and 50+—but these values are presented together to facilitate a more direct comparison to university figures.
b Respondents were allowed to select multiple responses for race and ethnicity. University demographics record race and ethnicity as a single value.
Analysis
Describing the Data
Demographic data describing responses to the student survey is seen in Table 1. Compared to the population of the university from which the sample was collected, White and Asian students were substantially overrepresented in the sample and respondents with the gender identity of Man/Male were substantially underrepresented. Responses for age range and class status were not substantially dissimilar from the university population.
Very few responses were received from the categories of race-American Indian or Alaska Native, race-Native Hawaiian or Other Pacific Islander, and race-Prefer not to say, so these values are included with race-White in the reference group in controls. Age range and class status were found to have high collinearity (rs(530)=.51, p<.001); therefore, class status was selected between the two to serve as the control variable used in tests. Ethnicity-Hispanic or Latino was found to have no significant correlation with other variables, so it was determined to be unnecessary to include it as a control variable.
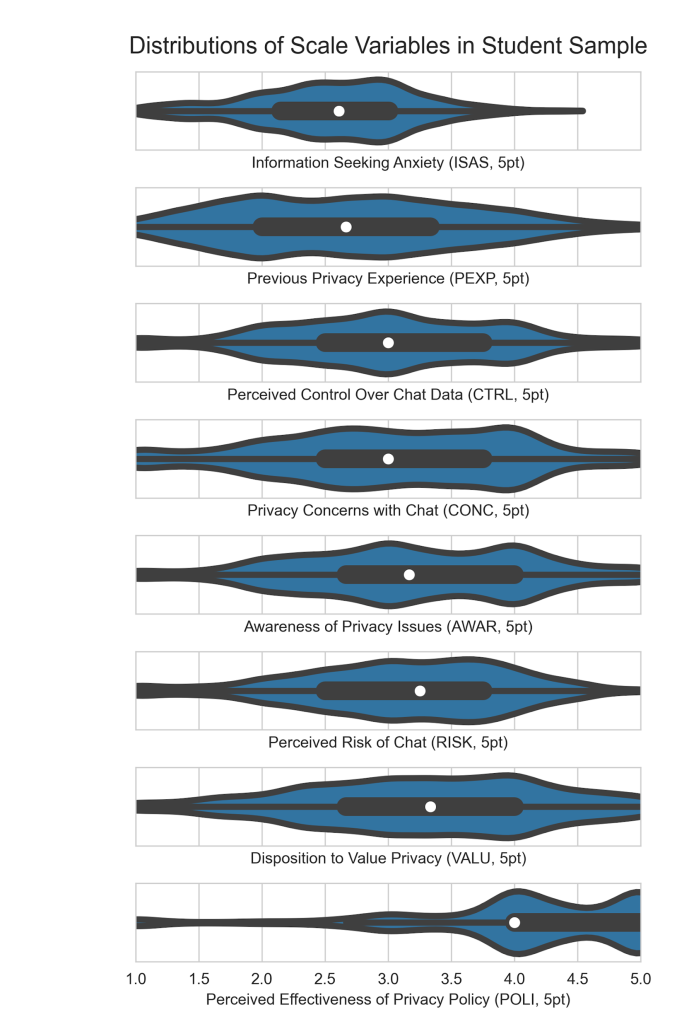
Individual response values to questions of the ISAS and the multiple privacy attitude scales were analyzed to confirm the validity of treating their summed scores as scale measurements. Consistent with best practices (Hayes & Coutes, 2020; Nájera Catalán, 2019; Revelle & Zinbarg, 2009), McDonald’s omega (𝜔) was used to calculate the internal consistency of each measurement scale and inter-item correlations were investigated. No values of 𝜔 were discovered to be below 0.734, indicating sufficient internal consistency. Only POLI was found to have an exceedingly high mean inter-item correlation at 0.812 indicating that questions may not be suitably distinct from one another; however, this value was considered acceptable for analysis as an independent variable (IV) in this study. Each scale measurement was normalized to a 5-point scale by calculating the mean value per respondent to facilitate comparison. Descriptive statistics for each measurement across the dataset were calculated. Only POLI was observed to deviate dramatically from a normal distribution, but this was also considered acceptable for analysis as an IV only. These values and the basic descriptive statistics for each scale measurement can be seen in Table 2. To visualize the shapes of these data, a plot of the median, interquartile range, and distribution for each scale measurement in order of lowest to highest median value is provided using violin plots in Figure 2.
Table 2. Reliability Analyses and Descriptive Statistics for Scale Measurements
| Reliability Measurements | Descriptive Statisticsa | |||||||
| Scale | N Items | ωb | Mean Inter-item Correlation |
Mean | Median | Std. Deviation | Skewness | Kurtosis |
| ISAS | 46 | 0.945 | 0.274 | 2.56 | 2.61 | 0.64 | -0.21 | -0.18 |
| CONC | 4 | 0.844 | 0.575 | 3.04 | 3.00 | 0.97 | -0.19 | -0.55 |
| RISK | 4 | 0.765 | 0.448 | 3.12 | 3.25 | 0.83 | -0.45 | -0.10 |
| CTRL | 4 | 0.798 | 0.498 | 3.01 | 3.00 | 0.87 | -0.06 | -0.32 |
| AWAR | 3 | 0.743 | 0.448 | 3.20 | 3.16 | 0.93 | -0.15 | -0.49 |
| PEXP | 3 | 0.734 | 0.396 | 2.70 | 2.67 | 0.93 | 0.21 | -0.72 |
| VALU | 3 | 0.797 | 0.513 | 3.29 | 3.33 | 0.95 | -0.25 | -0.53 |
| POLI | 3 | 0.929 | 0.812 | 4.08 | 4.00 | 0.93 | -1.43 | 2.29 |
a To determine these values, all scale measurements were normalized to a five-point scale by summing all responses and dividing by the number of items in the measurement instrument. b McDonald’s omega.
Testing Hypotheses
Following the CPM model proposed in Xu et al. (2011), both RISK and CTRL should both be affected by POLI and VALU, but RISK and CTRL are determined independently from each other. This study proposes to add Information Seeking Anxiety (ISAS), as a predictor alongside POLI and VALU, with a predicted effect on RISK and a potential additional effect on CTRL. As Xu et al. (2011) suggests, PEXP and AWAR should be used as controls.
To reduce the Type 1 error rate from multiple tests, a multivariate analysis of covariance was performed in which RISK and CTRL were dependent variables. Independent variables were ISAS, VALU, POLI, PEXP, and AWAR, plus several demographic variables found to have some correlation with privacy attitudes. An alpha threshold of .05 was used to determine statistical significance. Results from this analysis can be seen in Table 3.
Table 3. Multivariate Analysis of Covariance for Perceived Privacy Risk and Perceived Control Over Data
| Multivariate Model | RISK Modela | CTRL Modelb | |||||||||||
| Predictor | Pillai’s Trace | F | df | Error df | Sig. | β | F | Sig. | β | F | Sig. | ||
| Intercept | .164 | 51.186 | 2 | 521 | <.001 | 1.783 | 55.975 | <.001 | 1.698 | 33.429 | <.001 | ||
| ISAS | .027 | 7.223 | 2 | 521 | <.001 | .184 | 14.47 | <.001 | -.034 | .321 | .571 | ||
| VALU | .250 | 86.680 | 2 | 521 | <.001 | .448 | 167.4 | <.001 | .033 | .614 | .434 | ||
| POLI | .094 | 27.035 | 2 | 521 | <.001 | -.145 | 20.328 | <.001 | .251 | 40.455 | <.001 | ||
| AWAR | .030 | 8.061 | 2 | 521 | <.001 | -.052 | 1.909 | .168 | .180 | 15.391 | <.001 | ||
| PEXP | .012 | 3.243 | 2 | 521 | .040 | .030 | .775 | .379 | -.105 | 6.187 | .013 | ||
| race-Asian | .013 | 3.399 | 2 | 521 | .034 | .161 | 4.719 | .030 | .105 | 1.318 | .251 | ||
| race-Black or AA | .010 | 2.513 | 2 | 521 | .082 | .174 | 3.437 | .064 | .117 | 1.019 | .313 | ||
| gender-man/male | .009 | 2.463 | 2 | 521 | .086 | .057 | .781 | .377 | -.171 | 4.567 | .033 | ||
| class status-graduate student | .002 | .541 | 2 | 521 | .582 | -.048 | .454 | .501 | -.062 | .489 | .485 | ||
Table notes a R2 = .354 b R2 = .117
The following variables were found to have a statistically significant effect on the model: AWAR (Pillai’s Trace=.030, F2,521=8.061, p<.001); PEXP (Pillai’s Trace=.012, F2,521=3.243, p=.04); VALU (Pillai’s Trace=.250, F2,521=86.680, p<.001); POLI (Pillai’s Trace=.094, F2,521=27.035, p<.001); ISAS (Pillai’s Trace=.027, F2,521)=7.223, p<.001); and race-Asian (Pillai’s Trace=.013, F2,521=3.399, p=.034). The model was discovered to have a significant effect on both RISK (F9,522=31.718, p<.001) and CTRL (F9,522=5.288, p<.001). However, the explanatory power differed substantially between RISK (R2=.354) and CTRL (R2=.117).
Diagnostic tests were performed to ensure that necessary assumptions were met. Box’s M value of 32.984 (p=.596) retained the null hypothesis that covariance matrices between groups were assumed to be equal. Levene’s F tests against the model retained the null hypothesis that error variance was equal across groups for both RISK (F12,519=.725, p=.727) and CTRL (F12,519=.763, p=.689). The standardized residuals of both models were examined via normal Q-Q plots which did not indicate any significant deviation from normality. Kolmogorov-Smirnov normality tests were performed and retained the null hypotheses that residuals were normally distributed for both RISK (D532=.036, p=.092) and CTRL (D532=.025, p=.200). These results indicate that assumptions were met.
Holding all other variables constant, a one-point increase in the five-point ISAS was associated with an increase in the five-point RISK scale of 0.184 points but had no significant association with CTRL. The effect of ISAS on RISK exceeded that of POLI but trailed that of VALU. This result supports hypothesis H1 that information seeking anxiety increases the perceived privacy risk of live chat and rejects H10.
Discussion
Empirical Findings
Integrating the predictions of communication privacy management theory, library anxiety theory, and information seeking anxiety theory, the authors proposed that the perceived interpersonal threat present in library anxiety would carry to information seeking anxiety and that this sense of threat would affect the privacy risk-control assessment with library live chat by increasing the sense of perceived risk from privacy loss. In other words, students who were more worried about others judging them for having poor research skills would feel like they had more to lose from a lack of privacy and thus be more likely to think that using live chat was dangerous to their privacy.
Our analysis suggests that this hypothesis was indeed observed within the student responses to the survey. As information seeking anxiety increased, so too did the perception of privacy risk, even controlling for factors like other privacy attitudes and demographic differences.
This finding has interesting implications. It suggests that, although chat is assumed to be a preferable option for embarrassed students because of its increased anonymity, the more embarrassed students also felt a higher sense of privacy danger from chat. While one cannot say yet that this has an inhibiting effect on their use of chat, it certainly does suggest the potential. In the communication privacy management model, higher perception of risk is strongly associated with higher privacy concerns with a service in general. It also suggests that other relationships predicted between library anxiety, information seeking anxiety, and communication privacy management might exist.
Implications for Research
This study observed that increased information seeking anxiety is associated with a higher perception of privacy risk with chat. This finding lends credence to two conclusions. First, the use of Information Seeking Anxiety theory is a useful framework for investigating library anxiety in remote contexts. Second, the use of Communication Privacy Management theory is a useful framework for investigating the relationship between library anxiety/information seeking anxiety and privacy attitudes. More research is needed that explores other relationships between these theories. The authors hope to continue to explore these relationships using the dataset created for this study. Specifically, the direct relationship between information seeking anxiety and information privacy concerns should be examined and whether that relationship affects the use of live chat.
Implications for Practice
Library employees with a role involving live chat should familiarize themselves with the privacy concerns of students. These data suggest that interpersonal reference services like chat are sites for a higher perception of privacy risk. Librarians should take extra precautions to ensure perceived privacy risks of chat are proactively addressed. Reference strategies that do not depend on interpersonal interactions may be preferable to students with high information seeking anxiety. Continue to use open and welcoming language in online chats to reduce any anxiety students may have when asking for help, but use caution with language that could indicate to users that their chat could be connected to real-life social networks, as these findings indicate that a perception of interpersonal threat motivates a sense of higher privacy risk. For example, reconsider any practice of asking for identifying information (such as name, class, or instructor) that is not proactively volunteered. Likewise, avoid indicating that you are familiar with potentially identifying information, as you might by saying “I know your instructor well,” “I remember you from my instruction session,” or “You must be in Dr. Smith’s class,” etc.). Finally, one way you can reduce the need for information-anxious students to use interpersonal methods to ask for help is by assessing the chats for common questions and proactively updating the library’s web pages with that information in places users are most inclined to look.
Novelty
In the context of libraries, privacy is most often discussed through the lenses of information security or ethical practices (Magi & Garner, 2015), but literature which examines the effect of privacy on user attitudes and behavior regarding library services is scant. To the authors’ knowledge, this chapter is the first to apply communication privacy management theory to the context of library science and the experience of library users. In doing so, the authors also believe it to be the first time that a theoretical framework has been proposed to understand the behavior of library users in response to privacy attitudes.
This chapter is also novel in the literature of library anxiety, information seeking anxiety, and information privacy concerns. While much work has been done to understand the social antecedents of library anxiety and information seeking anxiety, here the authors show a novel example of a social consequence regarding privacy. Conversely, while the majority of research about information privacy concerns investigate its social consequences, here the authors show a novel example of a social antecedent regarding libraries and information seeking anxiety.
Conclusion
This chapter discusses experiential, theoretical, and empirical connections between library anxiety, privacy attitudes, and library live chat. The authors’ own experiences with providing live chat and analyzing chat data suggested that privacy concerns may reduce students’ willingness to use the live chat service. The literature of library anxiety and information privacy was explored to find theoretical evidence upon which to build empirical analyses. A specific connection was proposed between the perceived interpersonal threat in library anxiety, the application of information seeking anxiety to remote chat services, and the privacy risk-control assessment of communication privacy management theory. This connection predicted that anxiety related to seeking information leads to a perception that one’s personal privacy is at greater risk when using library live chat.
A dataset was constructed to test this prediction. It was revealed that the predicted effect was indeed observed. This suggests that the theoretical frameworks proposed here are a suitable foundation to explore similar relationships between privacy attitudes and the use of library reference services. These data suggest that interpersonal reference services like chat are sites for a higher perception of privacy risk. Implications for future research and library practice are explored.
References
Aghaei, F., Soleymani, M. R., & Rizi, H. A. (2017). Information seeking anxiety among M.A. students of Isfahan University of Medical Sciences. Journal of Education and Health Promotion, 6:14. https://doi.org/10.4103/jehp.jehp_88_14
Akhtar, S., & Abbasi, A. (2019). Privacy: Developmental, clinical, and cultural realms. Routledge.
Altman, I. (1977). Privacy regulation: Culturally universal or culturally specific? Journal of Social Issues, 33(3), 66–84. https://doi.org/10.1111/j.1540-4560.1977.tb01883.x
Anwar, M. A., Al-Kandari, N. M., & Al-Qallaf, C. L. (2004). Use of Bostick’s Library Anxiety Scale on undergraduate biological sciences students of Kuwait University. Library & Information Science Research, 26(2), 266–283. https://doi.org/10.1016/j.lisr.2004.01.007
Bostick, S. L. (1992). The development and validation of the Library Anxiety Scale (Order No. 9310624) [Doctoral Dissertation, Wayne State University] ProQuest Dissertation and Theses Global. https://www.proquest.com/docview/304002616/abstract/D3EC83A3F2D741B4PQ/1
Brown, L. J. (2011). Trending now—reference librarians: How reference librarians work to prevent library anxiety. Journal of Library Administration, 51(3), 309–317. https://doi.org/10.1080/01930826.2011.556950
Carlile, H. (2007). The implications of library anxiety for academic reference services: A review of literature. Australian Academic & Research Libraries, 38(2), 129–147. https://doi.org/10.1080/00048623.2007.10721282
Connaway, L. S., Radford, M. L., & OCLC Online Computer Library Center. (2011). Seeking synchronicity: Revelations and recommendations for virtual reference. OCLC Research. https://doi.org/10.25333/C3QK98
Erfanmanesh, M. (2016). Information seeking anxiety: Effects of gender, level of study and age. Library Philosophy and Practice, 1317, 1–20.
Erfanmanesh, M., Abrizah, A., & Karim, N. H. A. (2012). Development and validation of the Information Seeking Anxiety scale. Malaysian Journal of Library & Information Science, 17(1), 21–39.
Erfanmanesh, M., Abrizah, A., & Karim, N. H. A. (2014). The prevalence and correlates of information seeking anxiety in postgraduate students. Malaysian Journal of Library & Information Science, 19(2), 69–82.
Fagan, J. C., & Desai, C. M. (2002). Communication strategies for instant messaging and chat reference services. The Reference Librarian, 38(79–80), 121–155. https://doi.org/10.1300/J120v38n79_09
Givens, C. L. (2015). Information privacy fundamentals for librarians and information professionals. Rowman & Littlefield.
Gotschall, T., Gillum, S., Herring, P., Lambert, C., Collins, R., & Dexter, N. (2021). When one library door closes, another virtual one opens: A team response to the remote library, Medical Reference Services Quarterly, 40(1), 11–22. https://doi.org/10.1080/02763869.2021.1873612
Gray, S. M. (2000). Virtual reference services: Directions and agendas. Reference & User Services Quarterly, 39(4), 365–375. https://www.jstor.org/stable/20863842
Hanoch, Y., & Wood, S. (2021). The scams among us: Who falls prey and why. Current Directions in Psychological Science: a Journal of the American Psychological Society, 30(3), 260–266. https://doi.org/10.1177/0963721421995489
Hayes, A. F., & Coutts, J. J. (2020). Use omega rather than Cronbach’s alpha for estimating reliability. But…. Communication Methods and Measures, 14(1), 1–24. https://doi.org/10.1080/19312458.2020.1718629
Hoofnagle, C. J., King, J., Li, S., & Turow, J. (2010). How different are young adults from older adults when it comes to information privacy attitudes and policies? Social Science Research Network, 1–20. https://doi.org/10.2139/ssrn.1589864
Jan, S. U., Anwar, M. A., & Warraich, N. F. (2020). The relationship between emotional intelligence, library anxiety, and academic achievement among the university students. Journal of Librarianship and Information Science, 52(1), 237–248. https://doi.org/10.1177/0961000618790629
Jiao, Q. G., & Onwuegbuzie, A. J. (1997). Antecedents of library anxiety. The Library Quarterly: Information, Community, Policy, 67(4), 372–389. https://doi.org/10.1086/629972
Jiao, Q. G., & Onwuegbuzie, A. J. (1998). Perfectionism and library anxiety among graduate students. The Journal of Academic Librarianship, 24(5), 365–371. https://doi.org/10.1016/S0099-1333(98)90073-8
Jiao, Q. G., & Onwuegbuzie, A. J. (1999). Self-perception and library anxiety: An empirical study. Library Review, 48(3), 140–147. https://doi.org/10.1108/00242539910270312
Jiao, Q. G., & Onwuegbuzie, A. J. (2002). Dimensions of library anxiety and social interdependence: Implications for library services. Library Review, 51(2), 71–78. https://doi.org/10.1108/00242530210418837
Jiao, Q. G., & Onwuegbuzie, A. J. (2004). The impact of information technology on library anxiety: The role of computer attitudes. Information Technology and Libraries, 23(4), 138–144. https://doi.org/10.6017/ital.v23i4.9655
Kayhan, V. O., & Davis, C. J. (2016). Situational privacy concerns and antecedent factors. Journal of Computer Information Systems, 56(3), 228–237. https://doi.org/10.1080/08874417.2016.1153913
Keizer, G. (2012). Privacy (1st ed.). Picador.
Khan, S., Anwar, M. A., & Naveed, M. A. (2021). Prevalence and levels of information seeking anxiety among business students. Library Philosophy and Practice, 1–13.
Kuhlthau, C. C. (1988). Developing a model of the library search process: Cognitive and affective aspects. RQ, 28(2), 232–242. https://www.jstor.org/stable/25828262
Kuhlthau, C. C. (1991). Inside the search process: Information seeking from the user’s perspective. Journal of the American Society for Information Science, 42(5), 361–371. https://doi.org/10.1002/(SICI)1097-4571(199106)42:5%3C361::AID-ASI6%3E3.0.CO;2-%23
Kwon, N. (2008). A mixed-methods investigation of the relationship between critical thinking and library anxiety among undergraduate students in their information search process. College & Research Libraries, 69(2) https://doi.org/10.5860/crl.69.2.117
Logan, J., Barrett, K., & Pagotto, S. (2019). Dissatisfaction in chat reference users: A transcript analysis study. College & Research Libraries, 80(7), 925. https://doi.org/10.5860/crl.80.7.925
Magi, T., & Garnar, M. (2015). A history of ALA policy on intellectual freedom: A supplement to the intellectual freedom manual. American Library Association.
Malhotra, N. K., Kim, S. S., & Agarwal, J. (2004). Internet users’ information privacy concerns (IUIPC): The construct, the scale, and a causal model. Information Systems Research, 15(4), 336–355. https://www.jstor.org/stable/23015787
Mavodza, J. (2019). Interpreting library chat reference service transactions. The Reference Librarian, 60(2), 122–133. https://doi.org/10.1080/02763877.2019.1572571
Mawhinney, T. (2020). User preferences related to virtual reference services in an academic library. The Journal of Academic Librarianship, 46(1), 1–8 https://doi.org/10.1016/j.acalib.2019.102094
McAfee, E. L. (2018). Shame: The emotional basis of library anxiety. College & Research Libraries, 79(2), 237–256. https://doi.org/10.5860/crl.79.2.237
Mellon, C. A. (1986). Library anxiety: A grounded theory and its development. College & Research Libraries, 47(2), 160–165. https://doi.org/10.5860/crl_47_02_160
Mon, L., Bishop, B. W., McClure, C. R., McGilvray, J., Most, L., Milas, T. P., & Snead, J. T. (2009). The geography of virtual questioning. The Library Quarterly, 79(4), 393–420. https://doi.org/10.1086/605381
Mustofa, R. H. (2020). Is big data security essential for students to understand? Holistica: Journal of Business and Public Administration, 11(2), 161–170. https://doi.org/10.2478/hjbpa-2020-0026
Nájera Catalán, H. E. (2019). Reliability, population classification and weighting in multidimensional poverty measurement: A Monte Carlo study. Social Indicators Research, 142(3), 887–910. https://doi.org/10.1007/s11205-018-1950-z
Naveed, M. A., & Ameen, K. (2016a). A mixed-method investigation of information seeking anxiety in Pakistani research students. Pakistan and Information Science Journal, 47(1), 1–10.
Naveed, M. A., & Ameen, K. (2016b). Information seeking anxiety among postgraduate students of university. Journal of Behavioral Sciences, (26)1, 142–154. https://doi.org/10.4103%2Fjehp.jehp_88_14
Naveed, M. A., & Ameen, K. (2016c). Measuring levels of students’ anxiety in information seeking tasks. Pakistan Journal of International Management & Libraries, 17, 56–68. http://escholar.umt.edu.pk:8080/jspui/handle/123456789/3342
Naveed, M. A., & Ameen, K. (2017a). Determining the prevalence and correlates of information seeking anxiety among postgraduates in Pakistan. Libri, 67(3), 205–214. https://doi.org/10.1515/libri-2016-0017
Naveed, M. A., & Ameen, K. (2017b). A cross-cultural evaluation of the psychometric properties of Information Seeking Anxiety Scale in Pakistani environment. Malaysian Journal of Library & Information Science, 22(3), 35–51. https://doi.org/10.22452/mjlis.vol22no3.3
Nolen, D. S., Powers, A. C., Zhang, L., Xu, Y., Cannady, R. E., & Li, J. (2012). Moving beyond assumptions: The use of virtual reference data in an academic library. Portal: Libraries and the Academy, 12(1), 23–40. https://doi.org/10.1353/pla.2012.0006
Okazaki, S., Navarro-Bailón, M. Á., & Molina-Castillo, F.-J. (2012). Privacy concerns in quick response code mobile promotion: The role of social anxiety and situational involvement. International Journal of Electronic Commerce, 16(4), 91–120. https://doi.org/10.2753/JEC1086-4415160404
Onwuegbuzie, A. J., Jiao, Q. G., & Bostick, S. L. (2004). Library anxiety: Theory, research, and applications. University Press of America.
Owens, T. M. (2013). Communication, face saving, and anxiety at an academic library’s virtual reference service. Internet Reference Services Quarterly, 18(2), 139–168. https://doi.org/10.1080/10875301.2013.809043
Ozdemir, Z. D., Jeff Smith, H., & Benamati, J. H. (2017). Antecedents and outcomes of information privacy concerns in a peer context: An exploratory study. European Journal of Information Systems, 26(6), 642–660. https://doi.org/10.1057/s41303-017-0056-z
Petronio, S. (2002). Boundaries of privacy: Dialectics of disclosure. State University of New York Press. https://muse.jhu.edu/book/4588
Rahimi, M., & Bayat, Z. (2015). The relationship between online information seeking anxiety and English reading proficiency across gender. In Handbook of research on individual differences in computer-assisted language learning (pp. 449–468). IGI Global.
Revelle, W., & Zinbarg, R. E. (2009). Coefficients alpha, beta, omega, and the glb: Comments on Sijtsma. Psychometrika, 74(1), 145–154. https://doi.org/10.1007/s11336-008-9102-z
Reference and User Services Association (RUSA). (2017). Guidelines for implementing and maintaining virtual reference services. RUSA. https://www.ala.org/rusa/sites/ala.org.rusa/files/content/GuidelinesVirtualReference_2017.pdf
Smith, H. J., Dinev, T., & Xu, H. (2011). Information privacy research: An interdisciplinary review. MIS Quarterly, 989–1015. https://doi.org/10.2307/41409970
Smith, H. J., Milberg, S. J., & Burke, S. J. (1996). Information privacy: Measuring individuals’ concerns about organizational practices. MIS Quarterly, 20(2), 167–196. https://doi.org/10.2307/249477
Sutton, H. (2022). Protect students and staff from scams by providing proactive education, social media outreach. Student Affairs Today, 24(10), 5–11. https://doi.org/10.1002/say.31010
Taylor, D. A., & Altman, I. (1975). Self-disclosure as a function of reward-cost outcomes. Sociometry, 38(1), 18–31. https://doi.org/10.2307/2786231
University of North Carolina at Charlotte. (n.d.). About UNC Charlotte. https://admissions.charlotte.edu/about-unc-charlotte
University of North Carolina at Charlotte Institutional Research Analytics. (n.d.) Fact book: Fall 2020 – present. Institutional Research Analytics. Institutional Research Analytics. https://ir-analytics.charlotte.edu/fact-book
Van Kampen, D. J. (2004). Development and validation of the multidimensional library anxiety scale. College & Research Libraries, 65(1), 28–34. https://doi.org/10.5860/crl.65.1.28
Waldo, J., Lin, H. S., & Millett, L. I. (2010). Engaging privacy and information technology in a digital age: Executive summary. Journal of Privacy and Confidentiality, 2(1), 1–15. https://doi.org/10.29012/jpc.v2i1.580
Xu, H., Dinev, T., Smith, J., & Hart, P. (2011). Information privacy concerns: Linking individual perceptions with institutional privacy assurances. Journal of the Association for Information Systems, 12(12). http://doi.org/10.17705/1jais.00281

